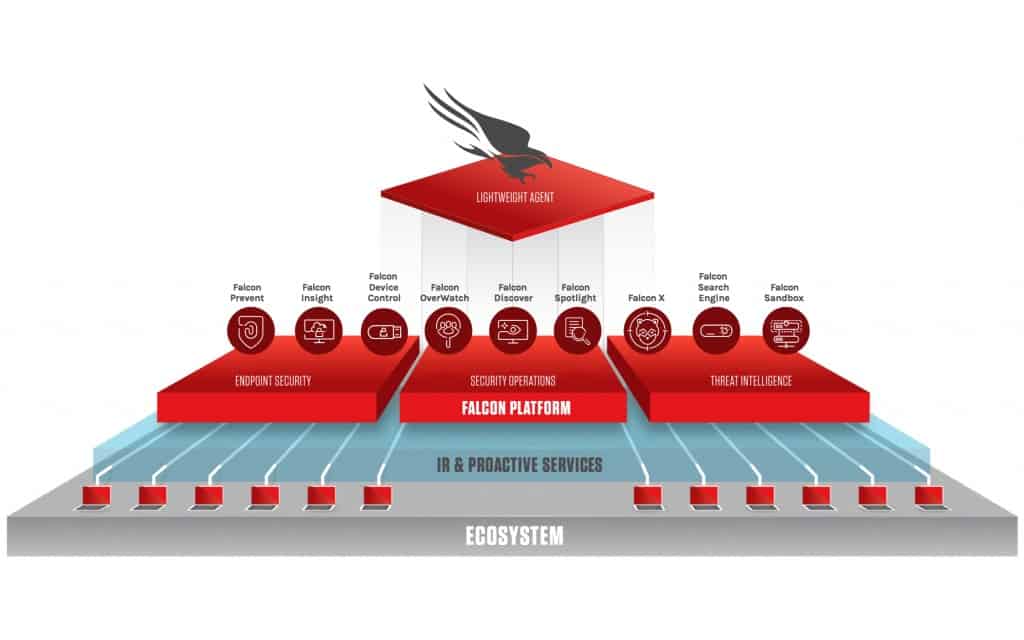
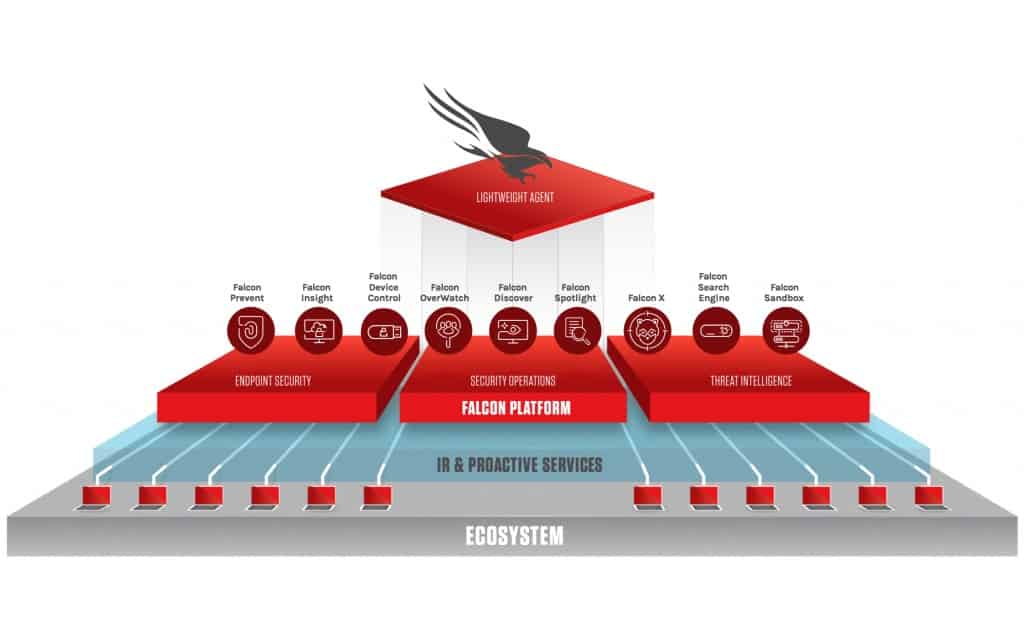
What Changed and Why It Matters
CrowdStrike terminated an employee it labeled a “suspicious insider” after screenshots of internal systems surfaced via the Scattered Lapsus$ Hunters group, which claimed to leverage data tied to a separate Gainsight incident. CrowdStrike says there was no compromise of its systems and no customer impact, and it referred the case to law enforcement. The business implication is clear: even top security vendors face insider and supplier-exposure risk, and session-cookie theft plus low‑bandwidth leaks (screenshots) can sidestep traditional defenses.
Key Takeaways
- No breach reported, but an insider allegedly shared internal screenshots and SSO session data; attackers reportedly offered $25,000 for access.
- Effective segmentation and rapid access revocation limited damage-an indicator of mature zero‑trust and least‑privilege controls.
- Supplier exposure matters: threat actors cited data from a Gainsight-related incident to aid social engineering and targeting.
- SSO cookie theft is a blind spot for many enterprises; device‑bound tokens, short lifetimes, and step‑up authentication are now table stakes.
- Buyers should press vendors on insider‑threat programs, screenshot/DLP controls, and third‑party access governance.
Breaking Down the Announcement
According to threat actor claims, the insider provided SSO authentication cookies and internal views for a cash payment. CrowdStrike states it detected suspicious behavior, revoked access, and found no evidence of production compromise or customer data exposure. The attackers framed their activity in the context of recent supplier breaches tied to Salesforce-connected ecosystems, including Gainsight. Whether or not the Gainsight angle materially contributed here, it highlights how third‑party data can improve spear‑phishing, credential harvesting, and insider recruitment.
Technical and Operational Reality
Two vectors matter for operators. First, screenshot exfiltration: it’s low volume, high signal, and often evades network DLP. Screens can reveal system names, ticket IDs, access paths, and even partial secrets. Endpoint controls that detect or restrict screen capture, watermark sensitive consoles, and log print‑screen events are underused-and frequently bypassed by personal phones if device separation policies are weak.
Second, SSO session artifacts: cookie or token replay can bypass passwords and MFA if tokens aren’t bound to a device or key. Mitigations include device‑bound session tokens (e.g., token binding/Proof‑of‑Possession), short cookie lifetimes, continuous access evaluation, step‑up MFA for administrative actions, and conditional access tied to hardware‑backed signals (FIDO2/WebAuthn, secure enclave attestation). For privileged roles, pair Just‑In‑Time elevation with ephemeral credentials and session recording, and isolate admin workflows on hardened devices or VDI.
Industry Context: Why Now
Scattered Lapsus$ Hunters reflects a playbook we’ve seen from Lapsus$ and Scattered Spider: target identity and people, not firewalls. Insider recruitment, contractor compromise, and third‑party pivots are cost‑effective and scalable. The wave of Salesforce‑adjacent supplier incidents created fresh target lists and context. For security vendors, the bar is higher-any insider lapse becomes a trust event, even when customers aren’t impacted.
What This Changes for Buyers
Procurement and vendor risk teams should treat “no breach” statements as necessary but not sufficient. Press your security providers on insider‑threat maturity: UEBA coverage for anomalous screenshot behavior, DLP for screen capture and clipboard, device posture checks for admin sessions, and break‑glass controls. Ask how production access is segmented, what percentage of admin actions require step‑up, how long tokens live, and whether session artifacts are device‑bound. For suppliers with Salesforce or success‑platform access, review OAuth scopes, IP allowlists, and token rotation policies.
Competitive Angle and Fit
This incident doesn’t demonstrate a product weakness unique to CrowdStrike; it exposes a category‑wide exposure: identity, insider risk, and supplier sprawl. Microsoft, Palo Alto Networks, SentinelOne, and others face the same realities. The differentiators now are programmatic: zero‑trust depth, insider‑threat telemetry, speed of containment, and transparency. Vendors that can prove device‑bound sessions for admin access, strong JIT/PAM, and effective screenshot/DLP controls will win trust in 2025 RFPs.
Risks and Open Questions
Open items include the full scope of what the insider shared beyond screenshots and whether any long‑lived tokens escaped revocation. While CrowdStrike reports no customer impact, enterprises should validate if any support pathways or delegated access could have been abused. Expect law enforcement timelines to limit disclosure; treat this as a stress test of your own assumptions rather than a one‑off headline.
Operator’s Recommendations
- Harden admin identity: enforce FIDO2/WebAuthn, device‑bound session tokens, short session lifetimes, and step‑up for privileged actions; implement JIT access with session recording.
- Control screenshots: enable endpoint policies that restrict or watermark screen capture for sensitive apps; separate admin work onto hardened or VDI endpoints without personal messaging apps.
- Tighten supplier access: review Salesforce‑adjacent vendors (e.g., Gainsight‑type integrations); minimize OAuth scopes, enforce IP allowlists, rotate tokens, and continuously monitor vendor behavior.
- Expand insider telemetry: deploy UEBA to flag anomalous capture behavior, token exports, and unusual admin console views; rehearse insider response playbooks with immediate access revocation and forensics.
- Validate with your vendors: request a written attestation of non‑impact, details on session revocation, and a summary of insider‑threat controls; update contracts to include right‑to‑audit for admin identity and DLP.
Leave a Reply